When you deal with traditional banks, you enjoy a safety net; if your card is lost or a technical error occurs, there is a central authority that can freeze the transaction and restore your rights. But in the world of Blockchain and Decentralization, the rules change radically.
There is no “Undo” button here, and there is no customer service agent with access to correct errors on your behalf. You are the bank, and you are solely responsible for protecting your vault.
This reality might seem scary at first, but it grants you immense power and total control if you learn the right rules.
This guide will simply explain how to protect your crypto from theft and intelligently avoid traps, ensuring your assets remain secure for years to come, far out of the reach of scammers.
What Is a Seed Phrase and Why Is It Your Most Dangerous Piece of Information?
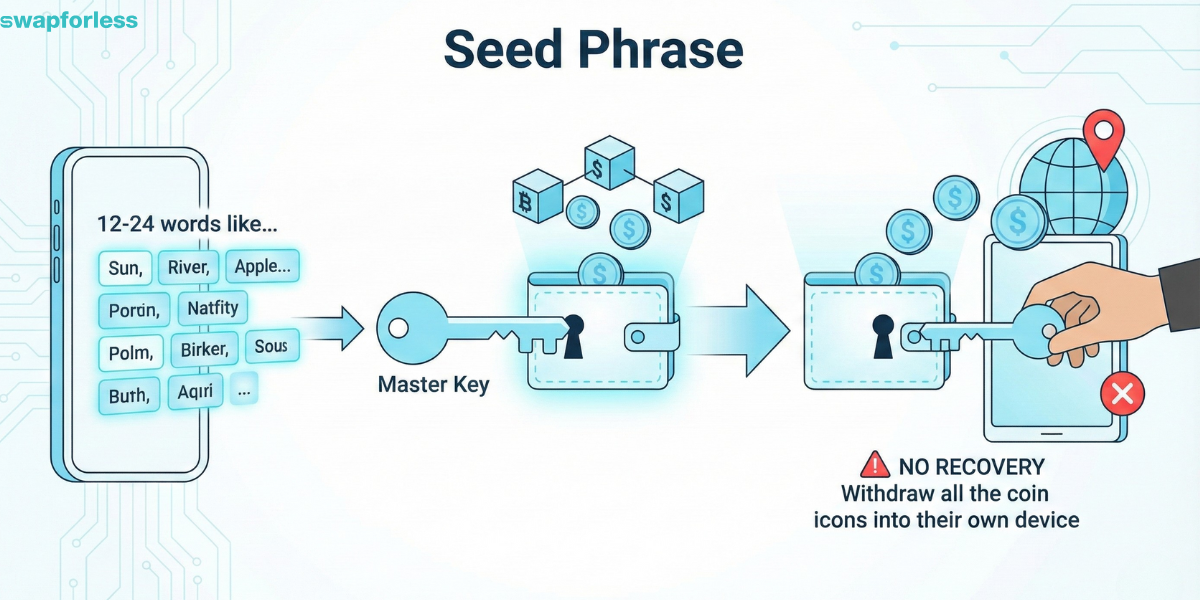
When you create a new digital wallet, the app gives you a sequence of 12 or 24 random English words (e.g., Sun, River, Apple, Sky…).
Seed phrase serve as a master key to regain access to your cryptocurrency wallet and its stored assets in the event of device loss or a forgotten password.
Whoever holds these words has full access to the funds. If someone else gets them, they can open your wallet from their device in another country and withdraw everything in seconds, and no entity in the world can stop them or recover the funds.
How to protect it?
- Do not photograph these words with your phone camera.
- Do not store them in your phone notes.
- Do not send them to yourself via email or chat apps. Anything connected to the internet is hackable.
- The Solution: Write them down with a pen on paper and store them in a very safe place in your home (like a personal safe).
What Is the Difference Between a Public Key and a Private Key?
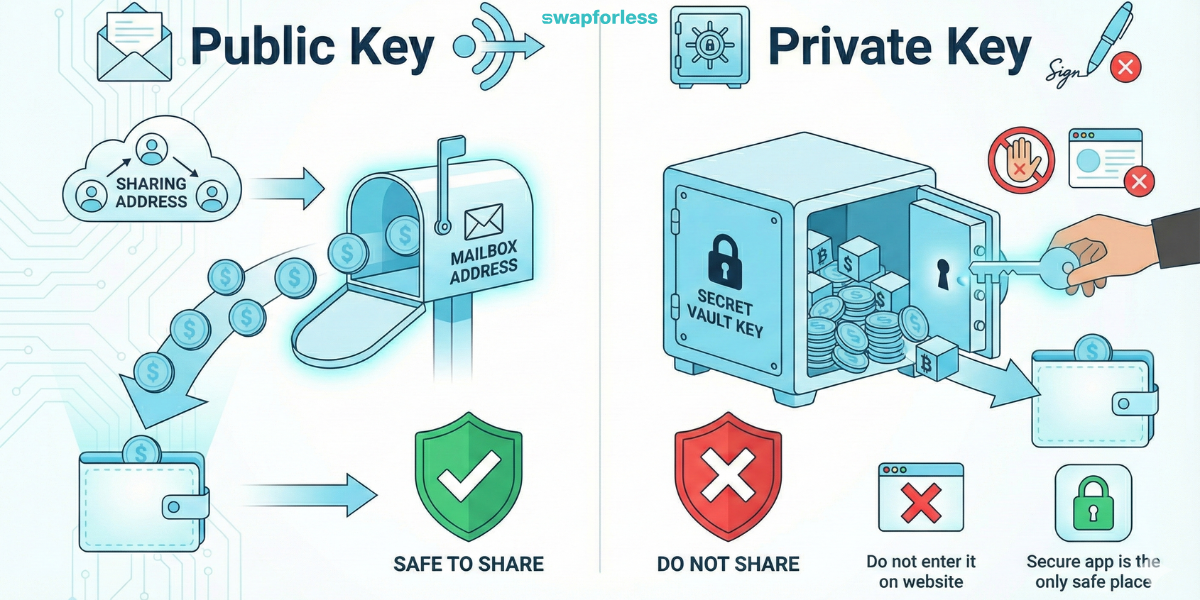
To understand the protection mechanisms, you must know what your digital wallet consists of. Every wallet relies on two keys:
-
Public Key: Imagine this key as your Bank Account Number (IBAN) or mailbox address. It is the address you share with others or put on platforms so they can send money to you. Sharing it is completely safe, and no one can steal your money just by knowing it.
-
Private Key: This is the real key to the vault or your secret digital signature. Whoever owns this key has total control over the assets and can move them in seconds. Never share this key with anyone, and never enter it on any website—only inside your wallet’s official app.
Cold Wallets vs Hot Wallets: Which is Safer?
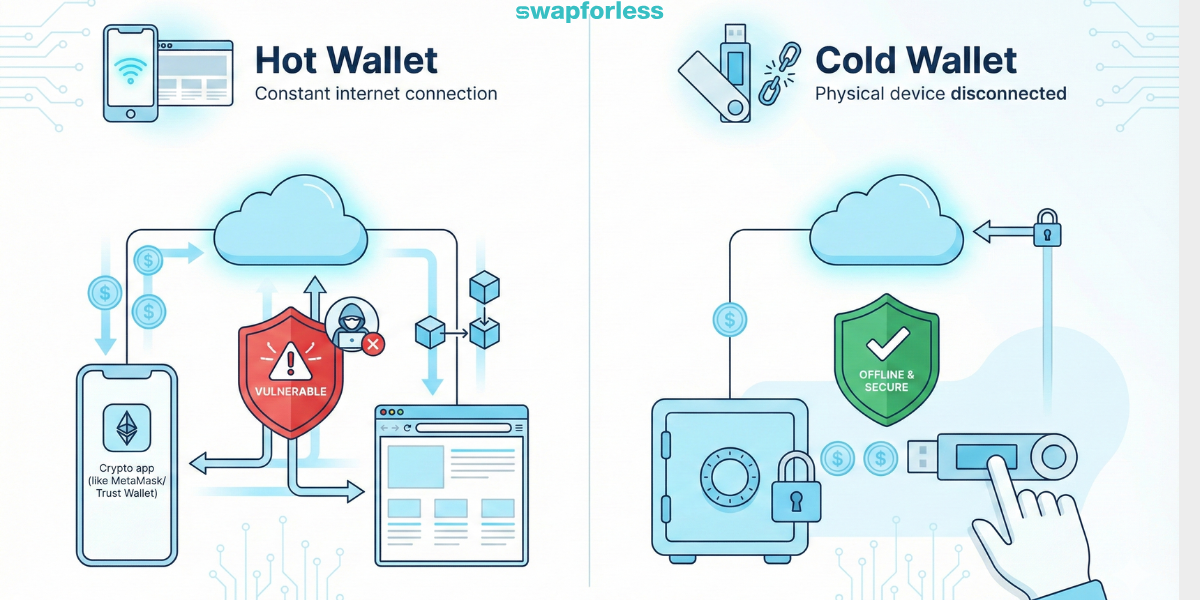
The fundamental difference lies in internet connectivity:
- Hot Wallets: These are apps or software permanently connected to the internet (like MetaMask or Trust Wallet). Their advantage is ease of access and speed, but their risk lies in being vulnerable to remote hacking if the device is compromised.
- Cold Wallets: These are physical devices resembling a USB drive (like Ledger or Trezor) that are completely offline and only connect when you need to execute a transfer, requiring you to press a physical button to confirm the transaction.
Pro Tip: Cold storage is the best and safest option for protecting your crypto, especially for large amounts you intend to hold for years.
What Is Two-Factor Authentication (2FA) and Why Is SMS Not Recommended?
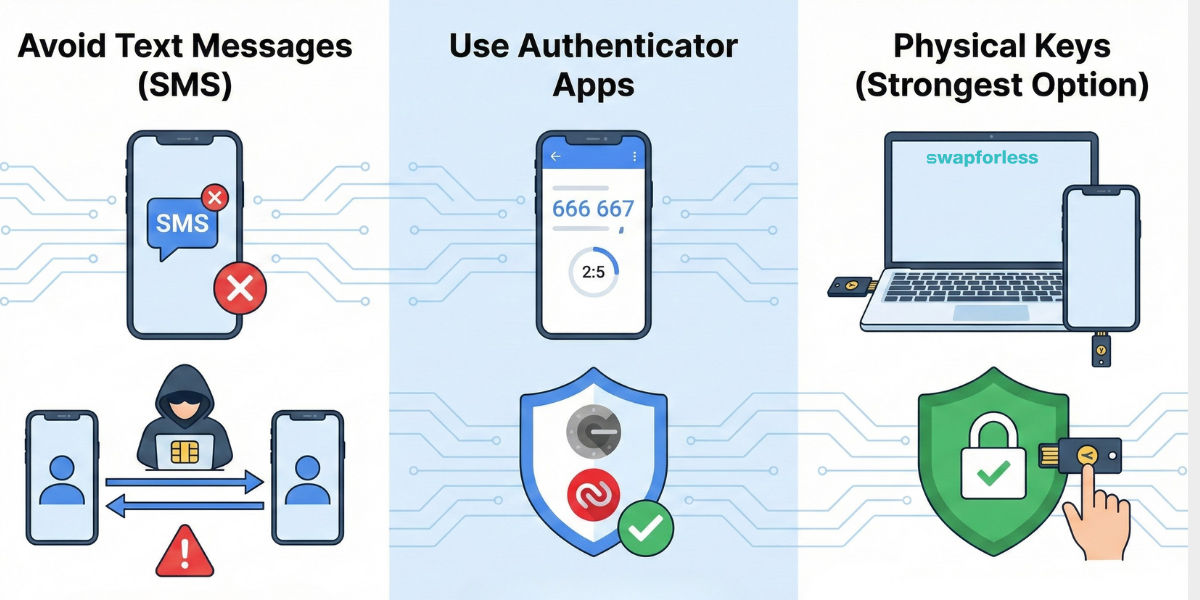
Two-Factor Authentication adds a second layer of protection to your accounts on centralized platforms. However, the method of authentication makes a huge difference in security levels:
- Avoid Text Messages (SMS): Hackers can use a trick called SIM Swapping, where they transfer your phone number to a SIM card they own, allowing them to receive your login codes.
- Use Authenticator Apps: Use apps like (Google Authenticator) or (Authy). These apps generate codes that change every 30 seconds and are not linked to the carrier network.
- Physical Keys (Strongest Option): Using real security keys like (YubiKey) requires inserting the key into the device to approve login, completely closing the door to remote hackers.
How Do Fraudsters Steal Money?
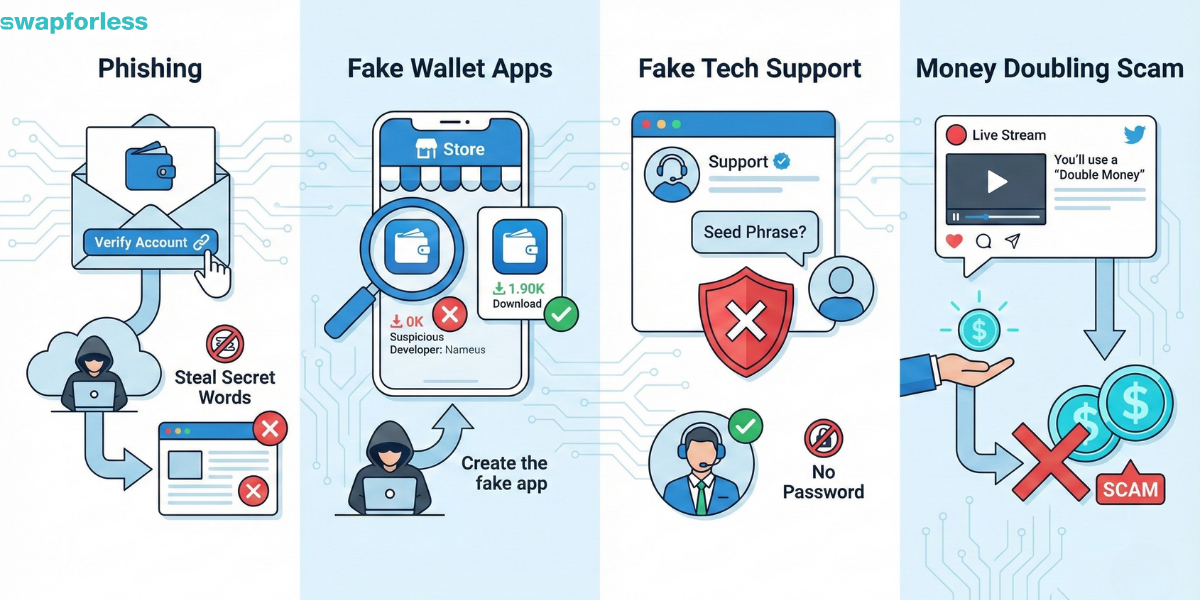
In 2025, hackers no longer try to break complex blockchain encryption (because it is nearly impossible). Instead, they try to hack your mind using psychological tricks. Here are the most famous traps:
1. Phishing: You receive an email that looks very official (bearing your wallet or exchange logo) asking you to “update your wallet” or “verify your account immediately to avoid closure,” with a link attached.
- The Truth: The link leads to a fake site that looks like the original, and its only mission is to steal your secret words.
- The Solution: Never click on any link in an email regarding crypto.
2. Fake Wallet Apps: You might find an app in the store that has the same name and logo as a famous wallet but is fake.
-
The Solution: Always check the developer’s name and download count, and download apps only from links found on the company’s official website.
3. Fake Tech Support: If you face a problem and post a complaint on social media, an account named “Support” will contact you immediately, asking for your seed phrase to solve the problem “manually.”
-
Remember: Real tech support will never ask you for passwords or seed phrases. Anyone who asks for them is definitely a thief.
4. The Money Doubling Scam: You might encounter a live stream or tweet inviting you to send an amount of crypto with a promise to return it doubled as part of a celebration. No one gives away money for free!
Read more about How to Get USDT Without Buying It Directly?
How to Spot Phishing Links Before Clicking?
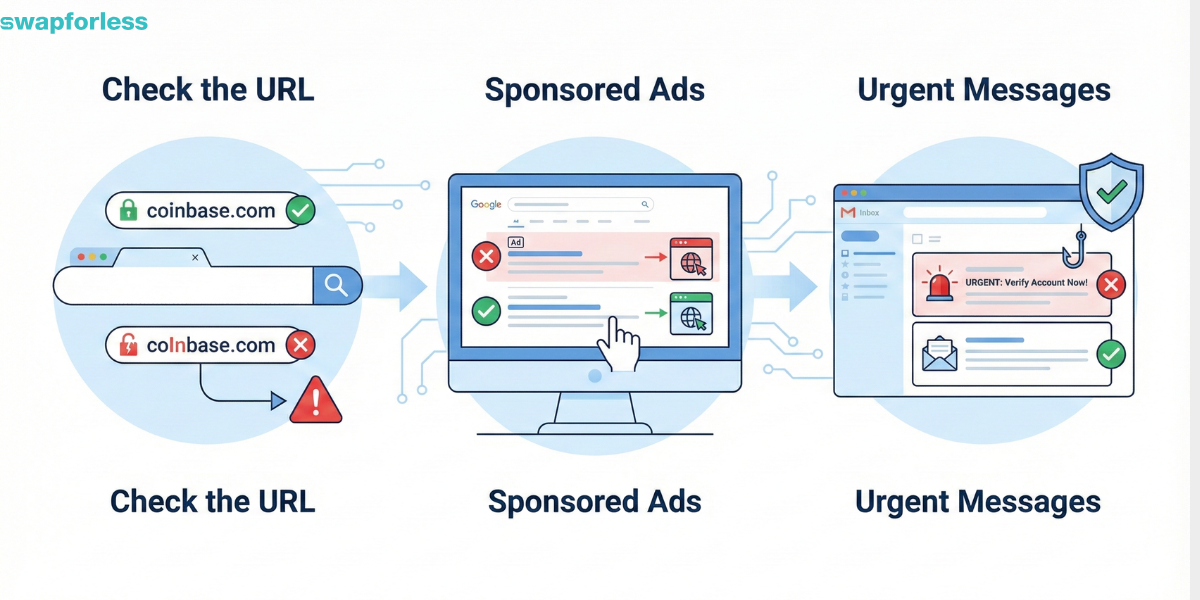
Digital fraud often relies on tricking the user into entering a fake site that looks exactly like the original and typing in their secret credentials. Signs that reveal the deception:
- Check the URL: Scammers change one letter that the eye misses easily (e.g., using coInbase.com instead of coinbase.com or replacing the letter ‘l’ with the number ‘1’).
- Sponsored Ads: Scam sites often appear in the first search results as an ad (Sponsored). Ignore ads and enter the official site directly by typing the address manually or using bookmarks.
- Urgent Messages: Any email asking you to confirm your identity “immediately” or your account will be closed is a scam attempt. Financial institutions do not request sensitive data via email in this manner.
How to Protect Your Device and Network When Handling Crypto?
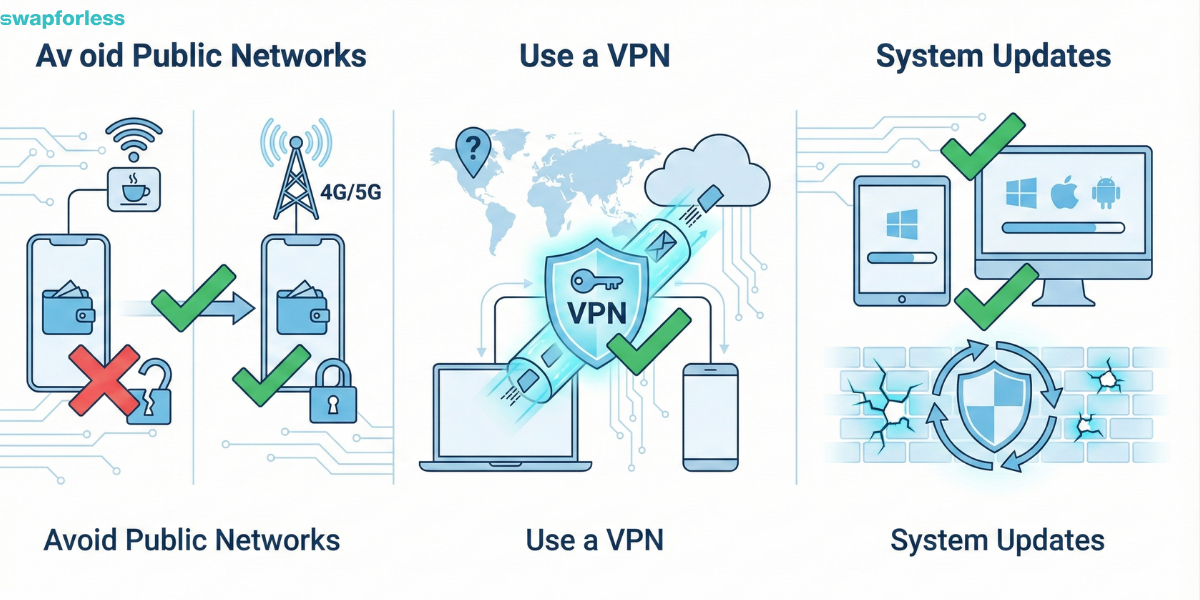
Digital security is an integrated system that starts with the device you use:
- Avoid Public Networks: Never open your wallet while connected to public Wi-Fi in a cafe or hotel. Use your own mobile data (4G/5G) only.
- Use a VPN: It is preferable to use a paid Virtual Private Network (VPN) to encrypt your connection data and hide your geographical location.
- System Updates: Security loopholes in operating systems (Windows, Android, iOS) are gateways for hackers. Continuous updates close these gaps.
Does Distributing Assets Across Multiple Wallets Reduce Risk?
Yes, applying the principle of “Don’t put all your eggs in one basket” is essential in digital security. If you own a large amount, divide it into:
- Main Cold Wallet (for the largest portion).
- Secondary Cold Wallet (backup).
- Trusted Exchange (for a small trading amount).
This measure ensures that in the worst-case scenario, if one entity is compromised, the rest of your assets remain safe elsewhere. This diversification minimizes potential damage.
Why Is Automated Exchange Safer Than Direct P2P?
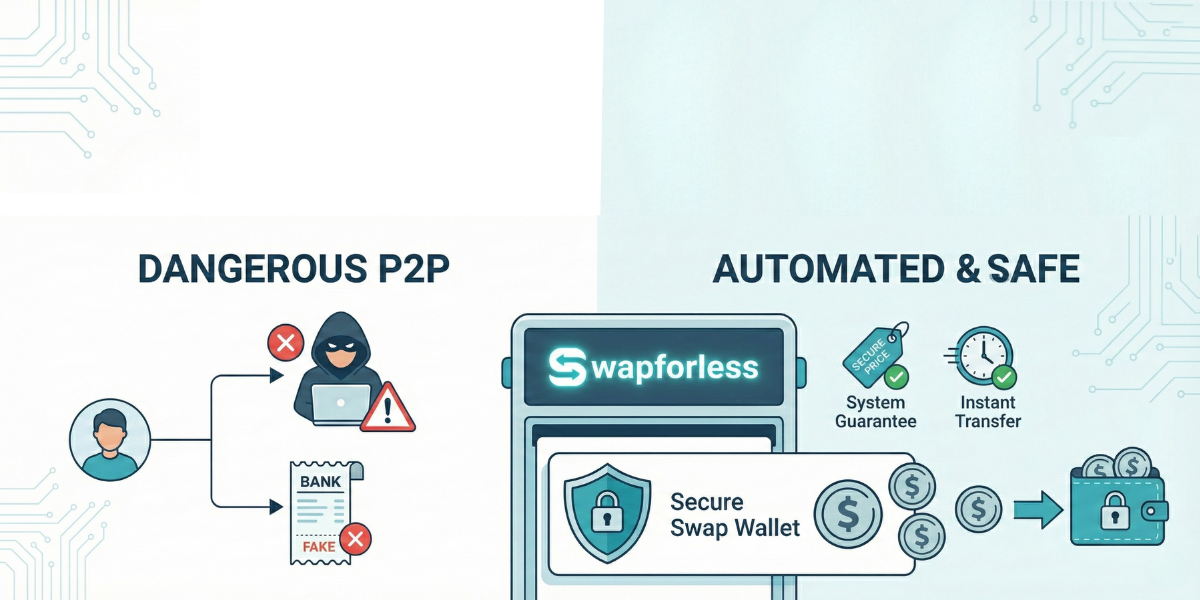
If you want to convert your balance (from gift cards to cash, or swapping between coins), some resort to finding brokers via social media groups (Random P2P).
This environment is the most dangerous of all. You might face “Triangle Fraud” (where the scammer makes you a party to a theft crime without your knowledge) or receive fake bank receipts.
The Safe Solution: Use reliable automated brokerage platforms like Swapforless that eliminate the human factor and its risks from the equation:
- System Guarantee: You are dealing with an automated system that guarantees the price and executes the transfer instantly without needing to trust a stranger.
- Swap Wallet: The platform provides a secure internal wallet to accumulate your small balances or hold them temporarily away from market volatility, giving you an extra layer of security for storing your assets before withdrawing them to your final wallet.
Read more about How to Consolidate Gift Card Balances in One Place?
In Conclusion
Security in the world of digital currency is not a product you buy; it is daily habits and constant vigilance.
Real protection starts with knowledge: protecting your keys, doubting every link and tempting offer, and using tools and platforms that put user safety first.
By applying these rules, you transform from an ordinary user at risk into a digital fortress that is hard to breach.
Read more: Send to 5 Digital Wallets Through swapforless website
 swapforless blog
swapforless blog



